The Ultimate Diet Guide
Expert tips and advice for achieving your health and fitness goals.
Counter-Terrorists Assemble: Ingenious Setups to Outsmart Your Opponents
Discover clever strategies and setups to outsmart your opponents in Counter-Terrorists Assemble—your ultimate guide to victory!
Top 10 Creative Strategies to Outsmart Terrorist Tactics
In today's complex world, outsmarting terrorist tactics requires innovative and adaptive strategies. Governments and security agencies are increasingly turning toward creative methods that not only neutralize threats but also prevent the radicalization of individuals. One noteworthy strategy is the use of data analytics and machine learning, which enables agencies to identify potential threats through patterns in social media behavior and communication networks. By analyzing these digital footprints, agencies can proactively disrupt plots before they materialize, showcasing how technology can be harnessed in the fight against terrorism.
Another effective strategy involves community engagement and education. Local communities play a critical role in identifying suspicious behaviors and fostering an environment that discourages extremist ideologies. Initiatives such as dialoguing programs and outreach efforts that promote inclusivity and cultural understanding can significantly reduce the allure of extremist narratives. By building trust and cooperation between communities and law enforcement, we can create a collective defense system that is not only resilient but also attuned to the unique challenges posed by terrorist tactics.
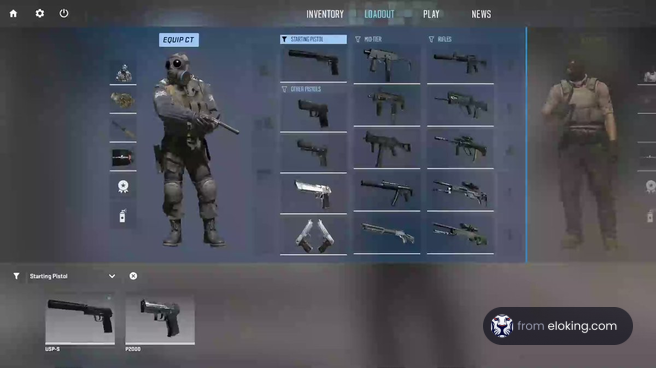
Counter-Strike, a popular first-person shooter, has evolved through various iterations, with Counter-Strike: Global Offensive (CS:GO) being one of the most influential. Players often enhance their gaming experience by utilizing specific strategies, such as csgo chat binds, to communicate effectively during matches.
How to Design Tactical Setups for Enhanced Counter-Terrorism Operations
Designing tactical setups for enhanced counter-terrorism operations requires a comprehensive understanding of both the operational environment and the specific threats at hand. To start, it's crucial to conduct a thorough threat assessment that identifies potential risks and vulnerabilities. This assessment should span various domains, including geographical, political, and socio-cultural factors that may influence the effectiveness of the operation. Once the risks are identified, strategic planning must follow, involving the development of clear objectives and identification of the necessary resources, such as personnel, equipment, and technology. This prepares teams to respond effectively in high-stakes situations.
Once the planning phase is complete, focus turns to the physical design of tactical setups. This involves creating adaptable and fortified locations, whether they're temporary bases or permanent facilities. Key elements to consider include:
- Surveillance capabilities: Implement advanced monitoring systems to gather real-time intelligence.
- Escape routes: Design multiple exits to ensure safe evacuation options.
- Communication systems: Establish secure lines for coordination among team members.
By integrating these components, units can enhance their operational readiness and resilience against evolving threats, making it essential for counter-terrorism operations to remain adaptable and responsive.
What Are the Most Effective Ingenious Setups Used by Counter-Terrorists?
Counter-terrorism strategies have evolved significantly over the years, utilizing various ingenious setups to mitigate threats effectively. One notable approach involves the integration of advanced technology and local intelligence networks. This includes the deployment of drone surveillance systems in crowded urban areas, allowing counter-terrorists to monitor suspicious activities in real-time. By establishing situational awareness through aerial views and high-definition cameras, they can identify potential threats before they escalate. Moreover, the collaboration with local community members fosters trust, yielding valuable intelligence that can thwart planned attacks.
Another effective setup involves the use of mobile response units that can be rapidly deployed to areas of concern. These units are often equipped with state-of-the-art weaponry and communication technology, enabling them to respond quickly to incidents. Furthermore, the use of simulation-based training for these units prepares them for various scenarios they might encounter in the field. This combination of prepared personnel and technology not only enhances operational effectiveness but also acts as a deterrent to potential attackers who are aware of such swift response capabilities.